Secure Shell (SSH) was first written in 1995 by Tatu Ylönen, a Finnish university researcher who developed the program after a hacker attempted to harvest passwords used in telnet and other login and remote administration protocols in use at that time.
The company, SSH Communications Security was formed shortly after that. Earlier in May, I had coffee with George Adams, the CEO of SSH, Inc, which is a publicly traded company on the Helsinki Exchange, with offices just down the road from me in Wellesley MA.
The old security idea that perimeter safeguards (firewall, remote access and VPN servers, SBCs and 802.1X authentication systems) are all you need is quite obsolete. The best practices in security use perimeter security for sure, but also apply strong authentication and privacy features to those internal services that are really sensitive to the successful operation of the corporation.
I use SSH (which came with Mac OS X) to login to my servers and manage database connections and the like which is where most applications of SSH reside – secure, remote login for system administrators. However, the standard implementation is not a scalable solution which is where the commercially available SSH Tectia offering fits.
The commercially available SSH Tectia does more than sysadmin secure sessions. It's security infrastructure can be used to enable secure FTP sessions, secure transparent TN3270 sessions and secure terminal access to servers. It's support for X.509 certificates on both the server and the client, assure strong authentication is also available.
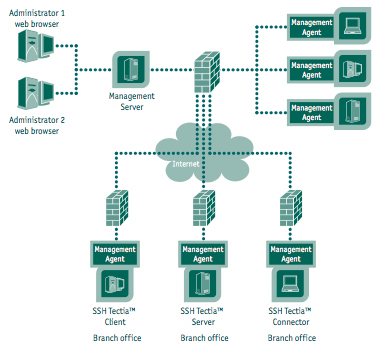
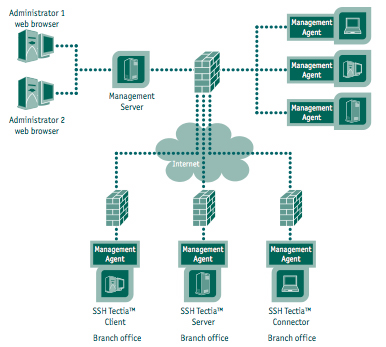
Tectia incorporates a client, a server and a security system administrator. The client and server editions are both optimized for a wide array of computer operating systems encompassing IBM zOS (mainframes), Linux, Solaris, AIX, HPUX and Windows computers and can be purchased online at the company's website. The mainframe client/server is able to access the IBM mainframe security acceleration hardware too.
The SSH Tectia Manager software is where scalability comes in. Here's where the management of the security policies are defined, automated and audited. The product includes links to the enterprise certificate authority (think Public Key Infrastructure) and APIs into software management applications (BMC), and can present meta data about syslogs, audit trails.
George and the company have taken significant steps to validate their technology with Visa, Mastercard to earn credible deployments in the financial services sector which is not just concerned with privacy of file transfers. They need audit-ability. They need to be able to adapt their security policies with the crank of a dial or flick of a software switch.
With annual revenues of $15 million and 80 people in the company, SSH Communications is well positioned to grow, by addressing the need for scalable infrastructure supervision.