I spoke with Kelly Anderson, CEO of Sendio about his company and the market. Kelly joined the company in November 2006 and brought in new sales leadership, marketing and CFO as part of the company's A round of venture capital funding.
I spoke with Kelly Anderson, CEO of Sendio about his company and the market. Kelly joined the company in November 2006 and brought in new sales leadership, marketing and CFO as part of the company's A round of venture capital funding.
Kelly explained that the I.C.E. Box solution delivers more than challenge-response functionality.
The Sendio implementation delivers 11 important email integrity services before sending a challenge only to the few unkown senders (some are optional):
- Sender checking – this makes sure that the domain the email purports to come from is in fact in compliance with domain standards and is actually registered. The logic is that only spammers use ill-formed 'from' addresses since they don't care about ever receiving a message.
- Recipient checking – checking to make sure the message is properly formed.
- Silver listing – SMTP enables a server to say to another server requesting to deliver a message, please try again later. In this way, every unknown sender's server meeting the sender check above is asked to send again. Since spambots can't afford to pause in their transmission processes, they have to just move on to the next message with the next server. Standards-compliant servers do pause and retry after a random delay.
- Anti-virus – leveraging an license agreement with Kaspersky Labs, Sendio checks the integrity of incoming and outgoing messages to assure email is not a vector for crimeware.
- Zero-Hour Recurrent Pattern Detection – the Commtouch technology forms the basis for identifying virus in their earliest and most dangerous states in the period between initial release and widespread availability of detection and remediation instructions.
- Attachment policy – administrators define what attachment types they'll accept and won't accept.
- Maximum number of recipients – messages with large numbers of recipients may be suspect. Administrators define this policy constraint.
- Message size limits disallows messages over a certain size.
- Sender Policy Framework is an extension to SMTP to reject forged email addresses optionally supported.
- DomainKeys Internet Mail is a platform for strong sender authentication. Recently offered as an IETF draft. Optionally supported.
- Bulk checker – using the Commtouch technology for Recurrent Pattern Detection, emails that had been sent to thousands of other users are flagged as bulk.
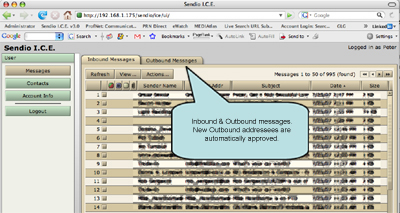 Here's a screen capture of the I.C.E. Box user interface. Users point their web browsers (Mac users use FireFox) to the server and authenticate themselves.
Here's a screen capture of the I.C.E. Box user interface. Users point their web browsers (Mac users use FireFox) to the server and authenticate themselves.
Users are presented with an unfiltered view of all messages currently in the holding queue, or all messages in the outbound queue.
The inbound queue contains messages have been challenged and are awaiting authentication by the sender. A maximum of 5000 messages are available for viewing at a time. At configuration time, administrators can establish the maximum life of messages in this queue. Users can and frequently do override the queue.
The outbound message queue is a service option that allows users to automatically add any new addressees to their approved lists. It also allows the I.C.E.Box to perform anti-virus and other optional policies on outbound messages such as attachment types or file size. It requires the email administrator to configure their email server to relay messages to the I.C.E.Box.
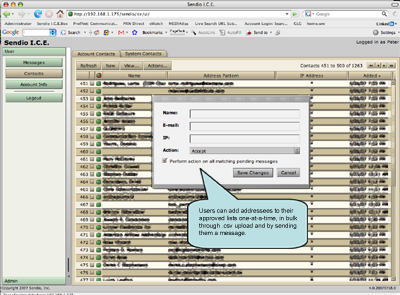 As shown in this screenshot, there is an option to add an addressee by hand, or through bulk upload using a .csv file.
As shown in this screenshot, there is an option to add an addressee by hand, or through bulk upload using a .csv file.
So, by sending an email to somebody not in the I.C.E. Box accept list they can be added to the accept list without being challenged.
In combination, the Sendio I.C.E.Box actually minimizes the occurrence of challenge to an incoming email from an unkown sender.
Packaging
The product is available in the classic appliance + service model or in a hardware-as-a-service model. There's no need for a server sizing process – small, medium, large – because the 1U package has plenty of processor power and tons of storage to handle most small business and medium enterprise needs. Sendio recommends clustering for larger organizations or for particularly complex email implementations.
Traction
The company has spent the last few months recruiting leading security systems resellers and educating them on the product and its capabilities. Even so, there is an impressive list of more than 250 enterprise customers to date.
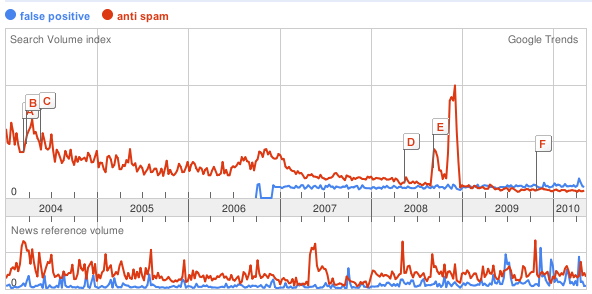
With all the news coming in about PDF-based spam as the next thing (filters can't correctly read PDFs either (they couldn't read image spam for the longest time – many still can't)), many users are recognizing that they need to change the way they process spam – in a way that respects users' time.
Clearly, performing anti-spam processes around sender authentication and anti-virus before challenging are important to reducing the size of the holding queue and make it easier for users to scan the queue for business-useful messages.