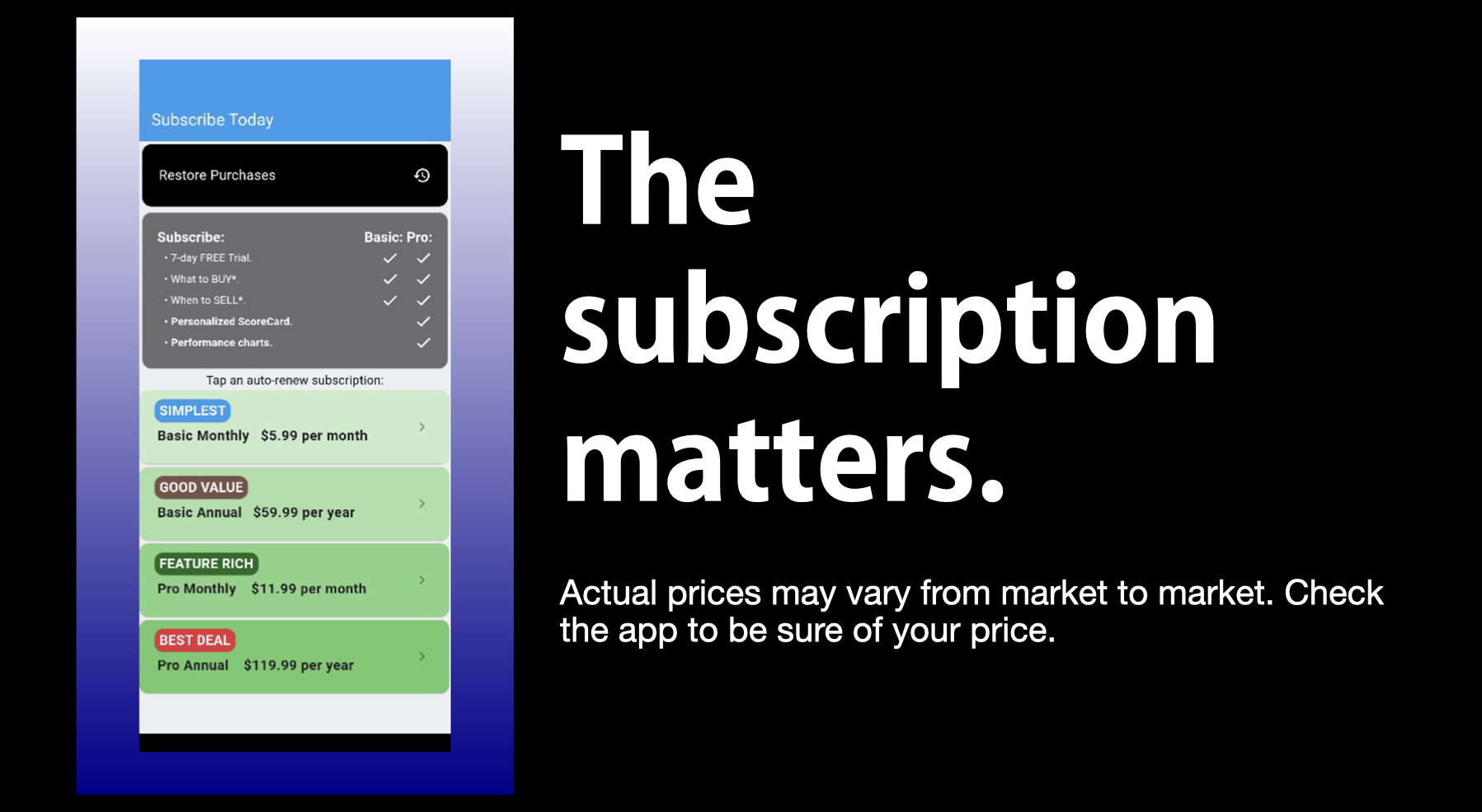
It signals the beginning of the end of the 'walled garden' oligopoly that is the wireless industry today.
It signals the beginning of the end of the 'walled garden' oligopoly that is the wireless industry today.
The mobile environment that we have enjoyed up to now is a 'walled garden.' All aspects of the service we experience are tightly controlled by the mobile operators. Now, to be fair these public companies (or divisions of public companies) have spent billions to create these safe and sterile environments and paid fair prices for the license to the spectrum, that finite public good managed by the FCC in the USA. Extracting a toll from every user and every content provider is the gist of their business model and as expected, this type of user taxation has serious dampening effects on usage, innovation and ultimately limits the utility of the service.
Of course, some would argue that this is a wonderful tradeoff forthe billions invested, the thousands employed and the utility derivedfor users.
This should remind you of the good ol' Bulletin Board days of the late1980s and early 1990s, before the commercialization of the Internet. Inthose days, [[CompuServe]], [[Prodigy (ISP)]] and [[AOL]] operated completenetworks of modem pools, packet networks and server farms controllingaccess, services and prices. Like the mobile environment of today, if aCompuServe user didn't like the service on CompuServe, they had to moveto another service provider and dial up there. If a content providerwanted more customers, they had to figure out how to post their contentonto the other service provider networks with each having their ownarcane rules and protocols and approaches causing high barriers toparticipation in innovation and experimentation.
Back then, computers were expensive, storage was even more expensiveand modems were fast at 9.6 kbps, blazing at 14.4 kbps and 56 kbps wasimpossible. [Not anymore. DSL generally starts at 700+ kpbs now.]
A walled garden has been necessary, according to the mobile operators,because like the pre-1968 (that was the year of the CarterPhonedecision) control assures that all devices generally behave as expected(with a few notable exceptions) and don't attack others or theintegrity of the mobile network. Raising the specter of the spamscourge, phishing attacks, distributed denial of service and othercyber-crimes that permeate the Internet today, mobile operators areplaying a delaying game. They hope to maintain their walled garden aslong as possible because that's the only way to maximize revenues.
Of course, it doesn't have to be this way.